
Quixxi Security
4.5
14
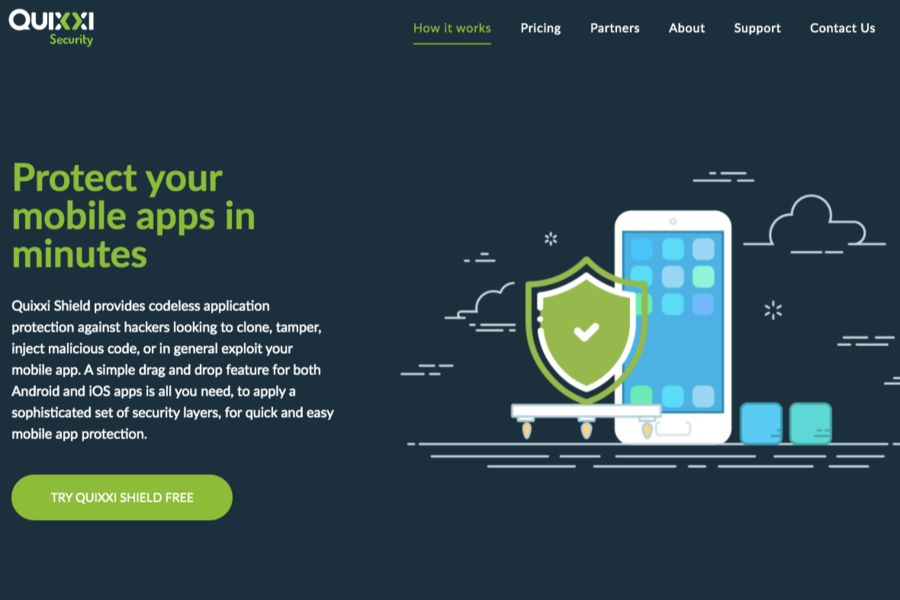
Quixxi Security provides codeless app protection against hackers looking to clone, tamper, inject malicious code, or exploit your mobile app. A simple drag & drop feature applies a sophisticated set of security layers, for quick & easy mobile app protection. Quixxi is also a monitoring tool with Licensing, Analytics & Diagnostics SDK. Allowing developers to identify illegal use & help recover associated lost revenue, detailed insights into customer engagement & advanced debugging files.
Ask anything of Quixxi Security with Workflos AI Assistant
https://quixxi.com
Apolo
Squeak squeak, I'm a cute squirrel working for Workflos and selling software.
I have extensive knowledge of our software products and am committed to
providing excellent customer service.
What are the pros and cons of the current application?
How are users evaluating the current application?
How secure is the current application?
Media











Quixxi Security Plan
Shield
99
2 apps / month
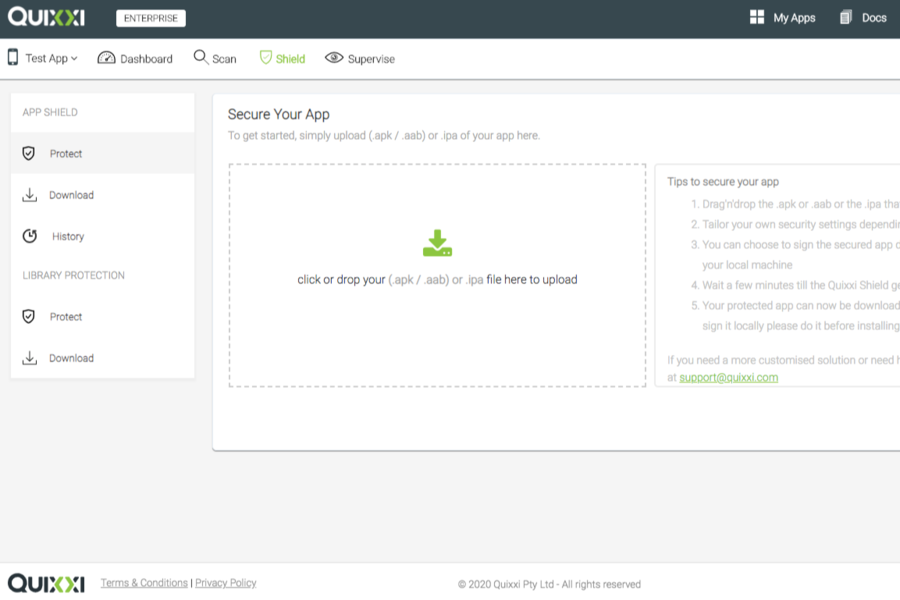
Quixxi Shield provides CODELESS application protection against hackers looking to clone, tamper, inject malicious code, or in general exploit your mobile app. A simple drag and drop feature applies a sophisticated set of security layers, for quick and easy mobile app protection.
Scan
9
2 apps / month
Quixxi Automated Vulnerability Assessment provides a detailed analysis of your app from a security perspective, reporting each detected vulnerability with a description, an explanation of the risks associated and recommendations for fixing the vulnerability. Incorporating OWASP, CVE/CVS vulnerability measures.













